If area programs similar to GPS had been hacked and knocked offline, a lot of the world would immediately be returned to the communications and navigation applied sciences of the Nineteen Fifties. But area cybersecurity is basically invisible to the general public at a time of heightened geopolitical tensions.
Cyberattacks on satellites have occurred because the Eighties, however the international wake-up alarm went off solely a few years in the past. An hour earlier than Russia’s invasion of Ukraine on Feb. 24, 2022, its authorities operatives hacked Viasat’s satellite-internet companies to chop off communications and create confusion in Ukraine.
I examine ethics and rising applied sciences and function an adviser to the U.S. Nationwide Area Council. My colleagues and I at California Polytechnic State College’s Ethics + Rising Sciences Group launched a U.S. Nationwide Science Basis-funded report on June 17, 2024, to clarify the issue of cyberattacks in area and assist anticipate novel and stunning situations.
Area and also you
Most individuals are unaware of the essential position that area programs play of their every day lives, by no means thoughts navy conflicts. For example, GPS makes use of alerts from satellites. GPS-enabled precision timing is important in monetary companies the place each element – similar to time of cost or withdrawal – must be faithfully captured and coordinated. Even making a cell phone name depends on exact coordination of time within the community.
Apart from navigation for airplanes, boats, automobiles and other people, GPS can be vital for coordinating fleets of vehicles that transport items to inventory native shops daily.
Earth-observation satellites are “eyes within the skies” with a novel vantage level to assist forecast the climate, monitor environmental adjustments, monitor and reply to pure disasters, increase agricultural crop yields, handle land and water use, monitor troop actions and far more. The lack of these and different area companies may very well be deadly to folks susceptible to pure disasters and crop failure. They might additionally put international economics and safety at severe danger.
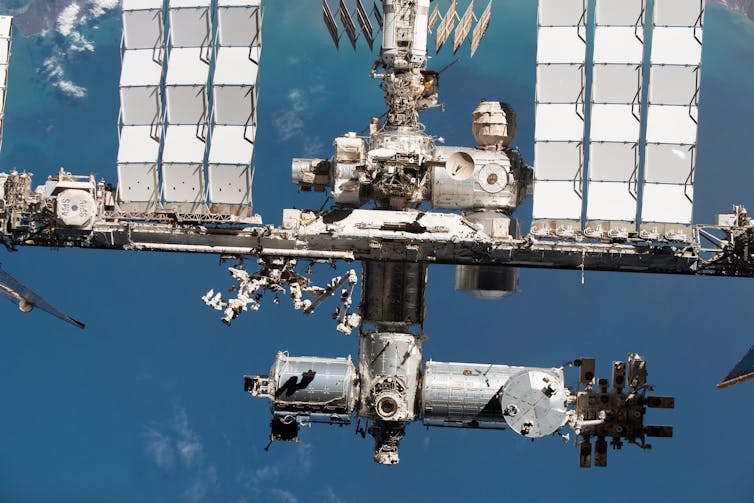
NASA
Components in play
In our report, we recognized a number of elements that contribute to the growing risk of area cyberattacks. For example, it’s vital to acknowledge that the world is at first of a new area race.
By all accounts, area is changing into extra congested and extra contested. Each nation-states and personal firms, that are underregulated and now personal a lot of the satellites in orbit, are gearing as much as compete for assets and analysis websites.
As a result of area is so distant and exhausting to entry, if somebody needed to assault an area system, they might possible must do it by way of a cyberattack. Area programs are notably engaging targets as a result of their {hardware} can’t be simply upgraded as soon as launched, and this insecurity worsens over time. As advanced programs, they will have lengthy provide chains, and extra hyperlinks within the chain improve the possibility of vulnerabilities. Main area initiatives are additionally challenged to maintain up with finest practices over the decade or extra wanted to construct them.
And the stakes are unusually excessive in area. Orbital trash zips round at speeds of 6 to 9 miles per second and might simply destroy a spacecraft on influence. It may well additionally finish area applications worldwide given the hypothesized Kessler syndrome wherein the Earth is ultimately imprisoned in a cocoon of particles. These penalties weigh in favor of area cyberattacks over bodily assaults as a result of the particles downside can be more likely to have an effect on the attacker.
Furthermore, given vital area infrastructure and companies, similar to GPS, conflicts in area can spark or add extra gas to a battle on Earth, even these in our on-line world. For example, Russia warned in 2022 that hacking certainly one of its satellites can be taken as a declaration of warfare, which was a dramatic escalation from earlier norms round warfare.
Conjuring situations
Even safety professionals who acknowledge the severity of this area cybersecurity risk face a serious problem. No less than in nonclassified boards, solely a few under-specified situations are sometimes thought of: one thing imprecise about satellite tv for pc hacking and one thing imprecise about alerts jamming or spoofing.
However failure to think about a full vary of potentialities could be devastating for safety planning, particularly towards hackers who’re a various set of entities with various motivations and targets. These variables are important to nail down as a result of they reveal clues about which methods and levers defenders might discover handiest in a response. For example, an assault by a state-sponsored hacker might require a distinct strategy than, say, one by a felony hacker after cash or by a chaos agent.
To assist with this piece of the safety puzzle, our report presents a taxonomy – the ICARUS matrix – that captures these variables and might create greater than 4 million distinctive combos of variables, which we name situation prompts. ICARUS is an acronym for “imagining cyberattacks to anticipate dangers distinctive to area.”
Listed below are three of the 42 situations we included within the report.
A 3D or additive printer could be a useful useful resource for shortly creating components on demand on area missions. A hacker might acquire entry to a printer on an area station and reprogram it to make tiny imperfections contained in the components it prints. A few of these built-to-fail elements may very well be components of vital programs.
NASA, CC BY-NC-ND
A hacker might corrupt the information from a planetary probe to indicate inaccurate atmospheric, temperature or water readings. Corrupted knowledge from a Mars rover, for instance, might falsely present that an space has vital subsurface water ice. Any subsequent mission launched to discover the positioning additional can be wasted.
In 1938, a radio drama about an alien assault instigated a panic when many listeners didn’t understand it was fictional. Equally, a hacker might entry the listening feeds of the Messaging Extraterrestrial Intelligence, or METI, venture and insert one thing resembling alien language in METI’s transcription. They might then leak it to the media, doubtlessly creating panic worldwide and transferring monetary markets.
Different situations in our report contain things like insider threats, AI vulnerabilities, false flag assaults, ecoterrorism, ransomware throughout a launch, in addition to extra distant situations about asteroid mining, off-world colonies and area pirates.
Tales for higher safety
Individuals are hardwired to answer tales, whether or not shared round prehistoric campfires or throughout digital platforms in the present day. Thus, crafting novel and stunning situations can assist deliver to life the invisible risk of area cyberattacks, in addition to highlight nuances throughout totally different situations which will require interdisciplinary specialists to sort out collectively.
Supply hyperlink



















